
A proven track record of delivering a resilient security posture to small, mid-market, and enterprise companies.
300,000+
servers covered
95%+
Less change noise
1,000’s
Companies secured
LOG MODE
Real-time automated detection
CimTrak logs all changes to target systems and applications, which can be analyzed and reported on.

UPDATE BASELINE
Dynamic version control
CimTrak stores an incremental “snapshot” of a file or configuration as changes occur. This feature allows for changes between snapshots to be analyzed and previous baselines to be restored or redeployed at any time.

RESTORE MODE
Immediate change reconciliation
CimTrak has the ability to instantaneously take action to reverse a change upon detection. This effectively allows a system to “self-heal”. CimTrak is the only integrity tool with this powerful feature.

DENY RIGHTS
Prevent unexpected change
On certain platforms, CimTrak can prevent changes entirely for those files and directories that should never change, avoiding the start of a security or compliance problem.
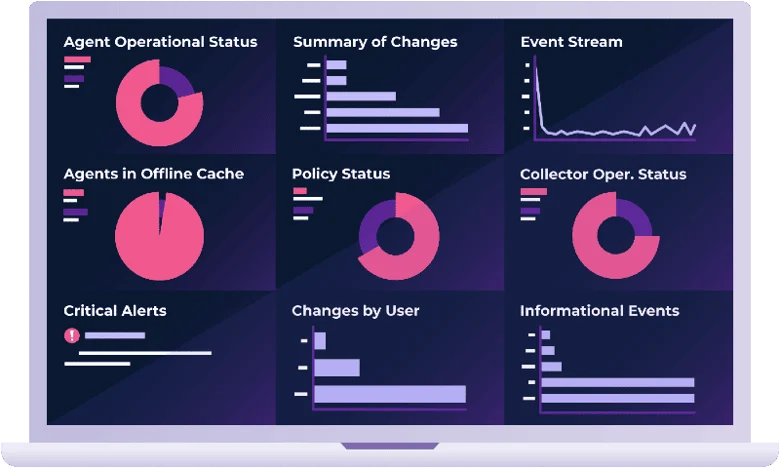
CIMTRAK DELIVERS CONTINUOUS SECURITY & AUTOMATED COMPLIANCE
Secure your entire IT infrastructure.

Identify threats before they hit.
Built-in threat intelligence provides additional context to determine is change is authorized.

Trusted File Registry
Reduce change noise and prevent false positives from known and good vendors that brings focus only to potentially malicious changes.

STIX/TAXII Thread Feeds
Protect yourself from malware and threat hashes via a blacklist that’s updated 24/7/365.

File Reputation
Integrate with Virus Total, Palo Alto Wildfire, or Checkpoint’s Threat API, to perform real time file and malware analysis of file changes.
Change reconciliation workflow & reporting.
Easy-to-use tool for managing change from the initial identification of the change to reconciling if the change was authorized and remediating if unwanted.
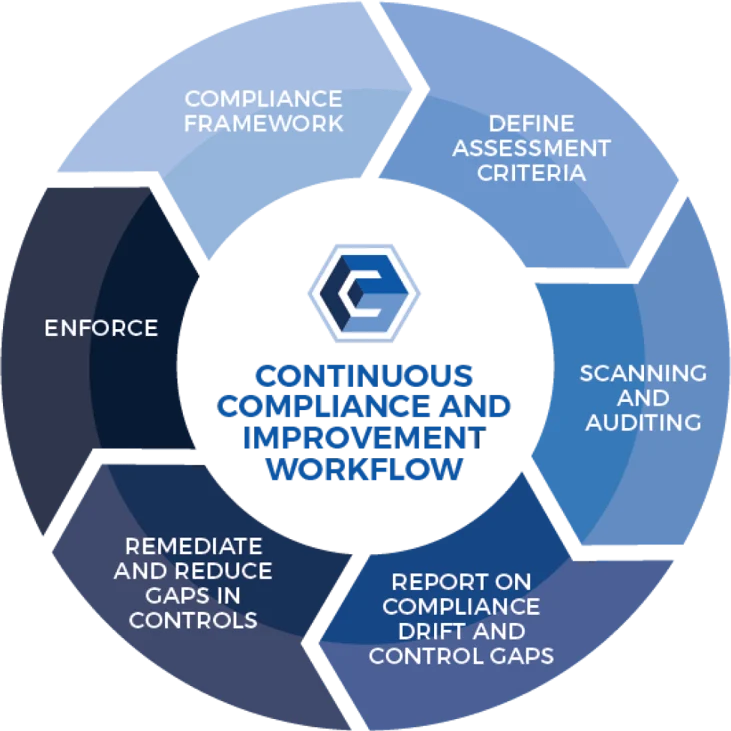
Continuously comply with major regulatory requirements.
Quickly establish, maintain and fix compliance requirements that improve the overall security and audit-readiness of your IT infrastructure.
Our Clients
USE CASES
Deploy CimTrak across your security stack to enhance monitoring, auditing, and change control processes.
Reduce the cost and complexity of detecting and remediating security problems resulting from unintended changes to your infrastructure in real-time.
Monitor changes to files across your organization
Protect against unauthorized changes to your network infrastructure.
Proactively protect critical ESXi Hyper-V applications to prevent unwanted or malicious changes.
Ensure Docker containers in AWS, Azure, and more are monitored for changes.
Proactively mitigate risk from unauthorized changes to your active directory.
Report on malicious or accidental changes in business-critical databases.
Thousands of security professionals across industries use CimTrak to protect critical IT assets.

Finance

Telecom

Healthcare

Energy & Utilities

Government

Education

Retail & Pos

Manufacturing
Why Systech
The key ingredient in the success of SYSTECH Technocraft Services is the spirit of our people and the strong value-adding culture we share. Our adaptability to new demands and opportunities is driven by more than entrepreneurial spirit. We grow with strong focus on customer and partner support which makes us easier to do business faster.
We work with strong network of reseller partners across India, to boost their business opportunities in cybersecurity, Infosec, analytics and cloud, helping them to achieve new revenues from the changing technology landscape.
Each of our regional business units is free to respond to its own instincts; applying its market experience and cultural awareness, not limited by protocol.
We are continually enhancing our distribution models. We know how to harness the potential of new technologies




























































