New Software Features! What’s in it for You?
There are a couple features in the latest release of Design-Expert and Stat-Ease 360 software programs (version 22.0) that I really love, and wanted to draw your attention to. These features are accessible to everyone, no matter if you are a novice or an expert in design of experiments. First, the Analysis Summary in the Post Analysis […]
The Benefits of File Sharing for Windows
There are a lot of Secure File Transfer (SFT) solutions out there, and a lot to consider when choosing which one is right for you. However, one of the primary criteria should be – what operating system are you running, and does your current solution have features to support it specifically? Secure file transfer is a […]
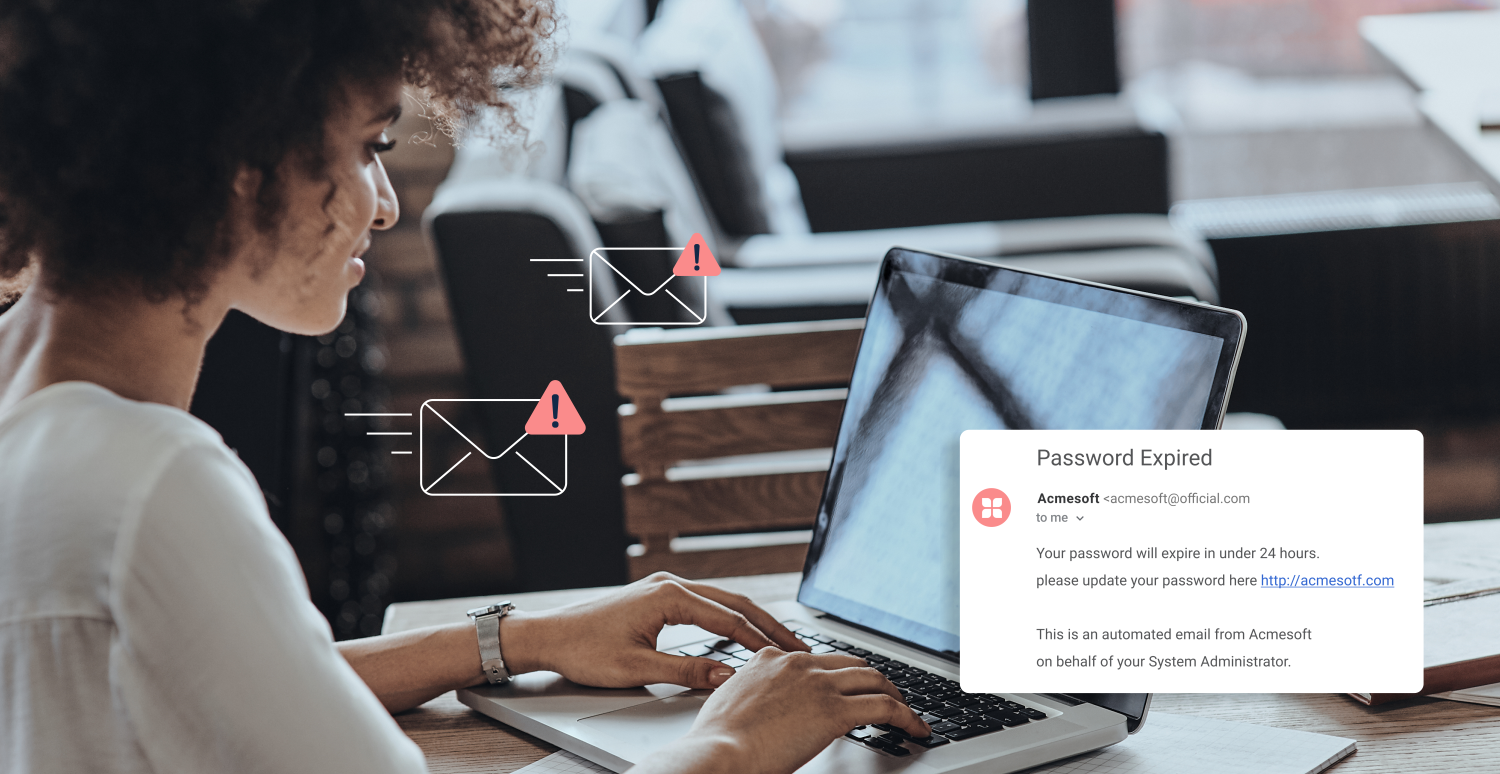
INFOGRAPHIC: How to Protect Your Data from Email Phishing Attacks
There are many different types of phishing scams, but email remains the most common of them all. Responding to a sender, clicking on a link, or downloading a file that may not be trustworthy can lead to data corruption, leaked confidential information, and infected devices or networks. Read the tips below or scroll down to view […]